Think of the seven layers as the assembly line in the computer. At each layer, certain things happen to the data that prepare it for the next layer. The seven layers, which separate into two sets, are:
Thursday, July 30, 2009
7 Layer of computer
Posted by Avatar at 3:15 PM 1 comments
Wednesday, July 22, 2009
Unlimited Gamez
Posted by Avatar at 10:03 PM 0 comments
Sunday, July 19, 2009
Time For Sport : Kalah Kita Bermaruah
Posted by Avatar at 6:58 PM 1 comments
Friday, May 15, 2009
Selamat Hari Guru 2009
Selamat hari guru kepada semua guru yg pernah mengajar saya dan yg mengajar saya pada tahun ini. Terlebih dahulu saya ingin memohon maaf kepada Pak G kerana telah mengecewakan harapan Pak G pada ujian selaras bulan april tetapi saya akan tingkatkan lagi usaha pada mid year ni.
Posted by Avatar at 9:09 PM 1 comments
Friday, April 17, 2009
Kelebihan solat berjemaah menurut teori fizik
kita mengandungi dua cas elektrik iatu cas positif dan cas negatif. Dalam
aktiviti harian kita sama ada bekerja, beriadah atau berehat, sudah tentu
banyak tenaga digunakan.
Dalam proses pembakaran tenaga, banyak berlaku pertukaran cas positif dan cas
negatif, yang menyebabkan ketidakseimbangan dalam tubuh kita.
Ketidakseimbangan cas dalam badan menyebabkan kita rasa letih dan lesu setelah
menjalankan aktiviti seharian. Oleh itu cas-cas ini perlu diseimbangkan semula
untuk mengembalikan kesegaran tubuh ke tahap normal.
Berkaitan dengan solat berjemaah, timbul persoalan di minda professor ini
mengapa Islam mensyariatkan solat berjemah dan mengapa solat lima waktu yang
didirikan orang Islam mempunyai bilangan rakaat yang tidak sama.
Hasil kajiannya mendapati bilangan rakaat yang berbeza dalam solat kita
bertindak menyeimbangkan cas-cas dalam badan kita. Semasa kita solat berjemaah,
kita disuruh meluruskan saf, bahu bertemu bahu dan bersentuhan tapak kaki.
Tindakan-tindakan yang dianjurkan semasa solat berjemaah itu mempunyai berbagai
kelebihan. Kajian sains mendapati sentuhan yang berlaku antara tubuh kita
dengan tubuh ahli jemaah lain yang berada di kiri dan kanan kita akan
menstabilkan kembali cas-cas yang diperlukan oleh tubuh. Ia berlaku apabila cas
yang berlebihan - sama ada negatif atau positif akan dikeluarkan, manakala yang
berkurangan akan ditarik ke dalam kita. Semakin lama pergeseran ini berlaku,
semakin seimbang cas dalam tubuh kita.
Menurut beliau lagi, setiap kali kita bangun dari tidur, badan kita akan merasa
segar dan sihat setelah berehat berapa jam. Ketika ini tubuh kita mengandungi
cas-cas positif dan negatif yang hampir seimbang. Oleh itu, kita hanya
memerlukan sedikit lagi proses pertukaran cas agar keseimbangan penuh dapat
dicapai. Sebab itu, solat Subuh didirikan 2 rakaat.
Seterusnya, setelah sehari kita bekerja kuat dan memerah otak semua cas ini
kembali tidak stabil akibat kehilangan cas lebih banyak daripada tubuh. Oleh
itu, kita memerlukan lebih banyak pertukaran cas. Solat jemaah yang
disyariatkan Islam berperanan untuk memulihkan keseimbangan cas-cas berkenaan.
Sebab itu, solat Zohor didirikan 4 rakaat untuk memberi ruang yang lebih kepada
proses pertukaran cas dakam tubuh.
Situasi yang sama turut berlaku di sebelah petang. Banyak tenaga dikeluarkan
ketika menyambung kembali tugas. Ini menyebabkan sekali lagi kita kehilangan
cas yang banyak. Seperti mana solat Zohor, 4 rakaat solat Asar yang dikerjakan
akan memberikan ruang kepada proses pertukaran cas dengan lebih lama.
Lazimnya, selepas waktu Asar dan pulang dari kerja kita tidak lagi melakukan
aktiviti-aktiviti yang banyak menggunakan tenaga. Masa yang diperuntukkan pula
tidak begitu lama. Maka, solat Maghrib hanya dikerjakan sebanyak 3 rakaat
adalah lebih sesuai dengan penggunaan tenaga yng kurang berbanding 2 waktu
sebelumnya.
Timbul persoalan di fikiran professor itu tentang solat Isyak yang mengandungi
4 rakaat. Logiknya, pada waktu malam kita tidak banyak melakukan aktiviti dan
sudah tentu tidak memerlukan proses pertukaran cas yang banyak.
Setelah kajian lanjut, didapati terdapat keistimewaan mengapa Allah
mensyariatkan 4 rakat dalam solat Isyak. Kita sedia maklum, umat Islam amat
digalakkan untuk tidur awal agar mampu bangun menunaikan tahajjud di sepertiga
malam. Ringkasnya, solat Isyak sebanyak 4 rakaat itu akan menstabilkan cas
dalam badan serta memberikan tenaga untuk kita bangun malam (qiamullail).
Dalam kajiannya, professor ini mendapati bahawa Islam adalah satu agama yang
lengkap dan istimewa. Segala amalan dan suruhan Allah Taala itu mempunyai
hikmah ynag tersirat untuk kebaikan umat Islam itu sendiri. Belaiu merasakan
betapa kerdilnya diri dan betapa hebatnya Pencipta alam ini. Akhirnya, dengan
hidayah Allah beliau memeluk agama Islam.
Posted by Avatar at 6:55 PM 2 comments
Sunday, April 5, 2009
Cekap IT : Memulihkan prestasi komputer yang Lembab
Di sini saya ingin berkongsi dengan rakan2 blog saya,
Posted by Avatar at 6:36 PM 1 comments
Friday, March 27, 2009
Petua Menguatkan Daya Ingatan
Sebagai seorang pelajar yang akan menghadapi pelbagai cabaran , daya ingatan amat penting untuk mengingati pelbagai ilmu yang kita pelajari.
Posted by Avatar at 10:54 AM 1 comments
Thursday, March 19, 2009
Macam mana nak main Playstation 2 di komputer ?
 Anda boleh mencuba bermain ps2 dalam pc dengan menggunakan PS2 emulator . Ianya boleh didapati di http://emulator-zone.com/doc.php/ps2/.
Anda boleh mencuba bermain ps2 dalam pc dengan menggunakan PS2 emulator . Ianya boleh didapati di http://emulator-zone.com/doc.php/ps2/.Posted by Avatar at 3:32 PM 1 comments
Wednesday, March 18, 2009
Time For Sport : The Kedah FA
The Kedah FA (Malay: Persatuan Bola Sepak Kedah) are a Malaysian professional football association team based in Kedah, Malaysia also enters a team in Malaysian football competitions to represent the state of Kedah. The team are also known by the nicknames Hijau-Kuning(The Green-Yellows) and Kenari (The Canaries). Kedah play in the Malaysia Super League, and are the most successful team in the history of Malaysian football after they have won a record of double treble titles in 2006-07 and 2007-08 seasons. The club were founded in 1924 by Tunku Yaacob Ibni Almarhum Sultan Abdul Hamid Halim Shah as a president, though they had limited success until the appointment of late Daro' Paduka Ahmad Basri Akil as manager in 1985. Under Dato' Ahmad Basri Kedah qualified to the 6Malaysia Cup final matches in seven years of period from 1987 to 1993; and won 2 Malaysia Cup titles, 1 league and FA Cup title. The club experienced a lean period during the 1980's and 1990s, but enjoyed a revival following the new millennium winning a cup treble in 2007 and 2008. Kedah has won the Malaysian league championship three times (1993, 2007 & 2008), the Malaysia Cup four times (1990, 1993, 2007 & 2008) and the Malaysia FA Cup three times (1996, 2007 & 2008). Jadi kepada penyokong kedah, doalah supaya tahun ini kedah akan menjuarai ketiga-tiga piala. PULUN !!!! KEDAH !!!! PULUN !!!!
Posted by Avatar at 8:23 PM 1 comments
Tuesday, March 3, 2009
How : To Speed Up an Internet Connection
If your Internet connection is slow, there are a number of methods to speed it up. Some of the following suggestions can be tried on the spot; others are more complex.
- Configure your browser so it won't display graphics, animations, sound, video or other multimedia content (see "How to Turn Off Sounds, Pictures or Video on Web Pages")
- Surf when Internet traffic is low. Heaviest traffic is usually on weekends and evenings.
- Use your cache effectively. "Cache" refers to storage space where your recently visited Web sites are saved. You may need to resize your cache allotment, or you may need to purge your cache periodically. Look through your browser's menus for items named Cache, Temporary Internet files and so on.
- Upgrade your modem. 56.6 kb/s modems are the fastest telephone modems available.
- Consult with your internet service provider to ensure that your modem is configured correctly.
- Replace your telephone modem with a fast-access connection such as wave, ISDN, DSL, satellite, a cable modem.
Posted by Avatar at 3:06 PM 0 comments
Sunday, March 1, 2009
How : To Remove the Black Worm Virus
- Navigate to the Symantec website. Download the W32.Blackmal@mm Removal Tool. Save the file to a location where you can easily find it. For example, save it to the desktop or create a "My Downloads" folder in the "My Documents" folder.
- Disconnect your computer from your LAN and from the Internet. Ensure that you log into an account with administrative privileges before continuing.
- Turn off System Restore if you are running Windows XP or Windows Me. In Windows Me, click Start and right-click My Computer. Click the Performance tab, click Properties, then click File System. Click the Troubleshooting tab and select the Disable System Restore check box. In Windows XP, click Start, right click My Computer and select Properties. Select the System Restore tab in the System Properties dialog box. Select the Turn Off System Restore check box. Click OK.
- Click Start > Run. Browse to the W32.Blackmal@mm Removal Tool filename. Click OK to begin the process of removing the Blackworm virus.
- Restart your computer. Run the Blackworm Removal Tool to ensure that the Blackworm virus is gone. Go back into system properties and reenable System Restore in Windows Me or Windows XP.
- Disable or password protect file sharing on all network computers, if applicable. Reconnect your computer to your network and to the Internet.
Posted by Avatar at 6:41 PM 0 comments
Thursday, February 26, 2009
V - Info : The Black Worm Virus
The Blackworm virus is malware which spreads itself primarily through email attachments. The risk varies depending on which version of the virus your computer has contracted.
The Blackworm virus can overwrite various document files, including Microsoft Word documents, Excel spreadsheets, compressed files such as .rar and .zip files, Portable Document Files and others. This document corruption takes place on the third day of every month.
It can also disable your antivirus software. So, be careful when you use your internet. I will tell you about how to remove the black worm in a new post.
Posted by Avatar at 9:54 PM 1 comments
Monday, February 23, 2009
How : To Make A Browser Run Faster
Who has time these days to wait for pages on the computer to switch? If you want to make your browser run faster read this step by step guide. You do not need to be a computer whiz to complete this task; but you do need to know what you are doing. So follow these steps and you will notice a difference in the how fast your browser .
- Click on your computer’s start button. This is located in the lower left hand part of your screen. A list of programs will appear.
- Click run which is usually located in the second column on the bottom. When the ‘run’ box pops up, type Msconfig in the run box and click ‘OK’.
- A second box will pop up. In this box uncheck everything you’re sure you don’t need and leave checked those programs that you are unsure of.
- Click on the Service Tab. This will list consuming programs that are sucking up your memory. The more you have running the slower your computer will be.
- Uncheck the following useless programs: Indexing Services, Error Reporting Services and Help and Support. Restart your computer. You will notice a difference in the speed of the use of your browser when you run it.
- Clear your Cache to make sure your browser is providing you with current versions of web pages that are stored on your web browser. To do so look under the tools option for internet options, then click General. Look for Temporary Internet Files. Click delete files, then click delete all offline content. Click OK, then click OK again. This will clear the cached webpages that are stored in the browser.
- Clear cookies, history and temporary internet files that is stored on your computer. To clear these go to start and click on ‘control panel.’ Click 'Network and Internet Connections,' then 'Internet Options.' Under the general tab, find the browsing history.
- Click ‘delete files,’ wait until it is done, click ‘delete cookies’ and wait until it is done, and then click ‘delete history,’ wait and then click ‘close’ and then ‘OK.' Complete these tasks as routine maintenance weekly to keep your browser up to speed.
Posted by Avatar at 3:21 PM 4 comments
Thursday, February 19, 2009
LA 1 : CPU
What is a CPU?
The Central Processing Unit, or CPU, is considered the brain of a computer. Without this vital component, the computer wouldn't be able do any of the functions it is capable of doing. Basically, it is a chip that handles the moving and processing of data.
With each new upgrade, the CPU is getting faster and more powerful. Speed and reliability is the name of the game when consumers are comparing CPU chips in the new PCs. For some, the brand of CPU is the major selling point for many when buying a new computer. The faster and more powerful the CPU, the more the computer will sell.
How Does it Work?
The CPU sits in the motherboard as the central unit. All of the other hardware components and programs installed on the system must go through the CPU before their function can be carried out. The CPU's job function is important and enormous in scale.
When a function, program or piece of data is called, the CPU pulls it from Random Access Memory (RAM) and any other hardware in order to process it. The CPU then reads the instructions associated to the task before sending it back to RAM. The instructions that the CPU receives pertains to calculations and data transportation. The system bus is the trail that the data must travel before it is executed. It is the CPU's job to make sure that the data is guided through the system bus to be processed by the CPU and then on to the next step. With every stop on the system bus, the CPU makes sure that the data gets there in the correct order.
Posted by Avatar at 3:04 PM 0 comments
Wednesday, February 18, 2009
How To Make Your Pc Faster
Is your computer slower than ever? Does it feel like your computer just can't open up programs? In this how to, it will teach you ways to make your computer faster. You can follow this step:
- The one way you can really boost your PC performance is by buying more ram to install in your computer. If you can go to a store and ask them to install more ram, that will help the computer run faster than before.
- Scan your computer for viruses and spyware. Make sure and get rid of any nasty viruses or spyware that are located in your computer. There are free programs for both problems such as, AVG free and Ad-aware. Get both and scan your computer.
- Get rid of unnecessary start up programs. The start up programs will load on your PC automatically and slow down your system. Click run and type in msconfig. Click on startup items and uncheck any useless start up programs.
- Run disk de-fragment and disk clean up. Both programs will be found in your accessory folder and both clean up the system.
If you want any software can help you to make your computer more faster, i can give you the latest sofware or antivirus such as tuneup utilities 2009,Speed Up Pc 4,Bitdefender 10 and extra.
Posted by Avatar at 6:38 PM 2 comments
Tuesday, February 17, 2009
LA 1 : Cyber Law
Cyber law describes the legal issues related to use of inter-networked information technology. It is less a distinct field of law in the way that property or contract are, as it is a domain covering many areas of law and regulation. Some leading topics include intellectual property, privacy, freedom of expression, and jurisdiction.
There are four types of Intellectual Property protection. They are patents for invention, trademarks for brand identity, designs for product appearance and copyright for material. Intellectual property laws are needed:
- to establish & safeguard the intellectual property which refers to works created by inventors, authors and artists.
- as businesses today continue to expand globally
Privacy can be protected by privacy law and utilities software.
Issues of jurisdiction have quickly come to the fore in the era of the Internet. The Internet does not tend to make geographical and jurisdictional boundaries clear, but Internet users remain in physical jurisdictions and are subject to laws independent of their presence on the Internet.As such, a single transaction may involve the laws of at least three jurisdictions:
1) the laws of the state/nation in which the user resides.
2) the laws of the state/nation that apply where the server hosting the transaction is located.
3) the laws of the state/nation which apply to the person or business with whom the transaction takes place.
Bacalah kut2 naik periksa.
Posted by Avatar at 3:03 PM 2 comments
Thursday, February 12, 2009
What Is Blog???
So what is blog?? Blog is a "Web log",usually maintained by an individual with regular entries of commentary, descriptions of events, or other material such as graphics or video. Entries are commonly displayed in reverse-chronological order. "Blog" can also be used as a verb, meaning to maintain or add content to a blog.
Many blogs provide commentary or news on a particular subject; others function as more personal online diaries. A typical blog combines text, images, and links to other blogs, Web pages, and other media related to its topic. The ability for readers to leave comments in an interactive format is an important part of many blogs. Most blogs are primarily textual, although some focus on art (artlog), photographs (photoblog), sketches (sketchblog), videos (vlog), music (MP3 blog), audio (podcasting), which are part of a wider network of social media.
Micro-blogging is another type of blogging, one which consists of blogs with very short posts. As of December 2007, blog search engine Technorati was tracking more than 112 million blogs. With the advent of video blogging, the word blog has taken on an even looser meaning — that of any bit of media wherein the subject expresses his opinion or simply talks about something.
Posted by Avatar at 9:08 PM 0 comments
Sunday, February 8, 2009
How to Be a Good Hacker
Hacking is a difficult process and if you don't have experience in this field, you might end up being on the wrong side of the law. Also if you are not certified as a hacker and you don't have permission from the owner to hack their computer, then it is illegal to hack someone else computer.
Step 1 :Learn a programming language. Python is a much easier programming language to learn then C++. Learning server side languages such as PHP will help you immensely.
Step 2 :Use a *nix terminal for commands. Cygwin will help emulate this for Windows users. The tools in this article can be found for Windows based machines. You should also consider using Linux or BSD, which are both more flexible, more reliable, and more secure.
Step 3 :Try securing your machine first. Make sure you fully understood all common techniques, including the way to protect yourself.
Step 4 :Know your target. The process of gathering information about your target is known as 'enumeration'. You can use the ping utility to see if the target is 'alive, don't trust the results of the the ping utility as it uses the ICMP protocol and easily be shut down by system administrators.
Step 5 :Determine the operating system (OS). This is important because how can you gain access to a system if you don't know what the system is!. Try pOf, or nmap to run a port scan. This will show the ports that are open on the machine, the OS, and can even tell you what type of firewall or router they are using so you can plan a course of action.
Step 6 :Find some path or open port in the system. Common ports such as FTP (21) and HTTP (80) are often well protected, and possibly only vulnerable to exploits yet to be discovered. An open port 22 is usually evidence of an SSH service running on the target, which can sometimes be brute forced.
Step 7 :Crack the password or authentication process. There are several methods for cracking a password, including brute force. Using brute force on a password is an effort to try every possible password contained within a pre-defined dictionary of brute force software. You may try using Rainbow Tables for fastest password cracking.
Step 8 :Get super user (root) privileges if targeting a *nix machine, or administrator privileges if taking Windows systems. To see all the files on a computer you need super user privileges. For routers this is the "admin" account by default for Windows, this is the Administrator account, etc.
Step 9 :Use various tricks. Often to gain super user status you have use tactics such as creating a "buffer overflow" which is basically causing the memory to dump and allowing you to inject a code or perform a task at a higher level then you're normally authorized.
Step 10 :Create a backdoor. nce you gained full control over machine, it's best to make sure you can come back one day. This can be done by backdooring important system service, such as SSH server. Your backdoor may be removed upon next system upgrade, so only experienced hackers would backdoor the compiler itself, so using compiled software would be a way to come back.
Step 11 :Cover your tracks. Never ever let the administrator know that the system is compromised. Do not change the website, do not create more files than you really need. Act as fast as possible. If you patched a server like SSHD, make sure it has your secret password hard-coded.
Posted by Avatar at 9:04 PM 1 comments
Labels: Hacker
Friday, February 6, 2009
Arithmetic logic unit

This was an arithmetic logic unit you sit back and admire. It was part of Honeywell's Datamatic 1000 computer. (Image courtesy of Honeywell, Inc.)
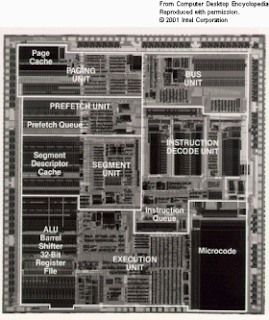
Thirty Years Later
The ALU embedded within this 386 chip would fit on the end of a pencil eraser with room to spare. (Image courtesy of Intel Corporation.)
In computing, an arithmetic logic unit (ALU) is a digital circuit that performs arithmetic and logical operations. The ALU is a fundamental building block of the central processing unit (CPU) of a computer, and even the simplest microprocessors contain one for purposes such as maintaining timers. The processors found inside modern CPUs and graphics processing units (GPUs) have inside them very powerful and very complex ALUs; a single component may contain a number of ALUs.
Mathematician John von Neumann proposed the ALU concept in 1945, when he wrote a report on the foundations for a new computer called the EDVAC.

A typical schematic symbol for an ALU: A & B are the data (registers); R is the output; F is the Operand (instruction) from the Control Unit; D is an output status.
Posted by Avatar at 8:23 AM 2 comments
Thursday, February 5, 2009
V-Info: How to make a virus
I used to think that making viruses had something to do with programming skills. I thought writing a program that could copy itself, spread itself, hide in other programs or files, find its way around on all these different computers, that surely had to be the summum of programming.
- Search the web for something like "Virus Construction Tool" or "Internet Worm Generator". Download it.
- Run the program (click on its icon).
- Fill in the form. Choose interesting names.
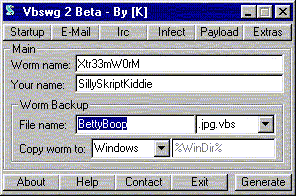
4. Check the boxes to indicate how you want this virus / worm to spread (e-mail, irc, ...)
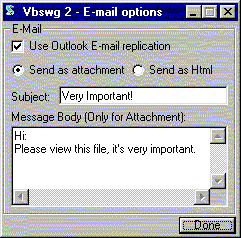
5. Choose your options for 'payload'
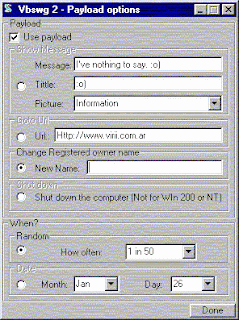
6. Then click "Done".
8. Save the file
9. Run it to see if it works
Posted by Avatar at 3:27 PM 1 comments
Wednesday, February 4, 2009
Akibat Tak Buat Kerja
Hari ini merupakan hari yang malang buat sesiapa tak buat kerja ICT. Hampir 95% daripada seluruh murid dalam kelas didenda kerana x buat dan tak siap nota...
Denda yang dikenakan untuk x buat nota tu sebenarnya adalah pumping 25 kali tapi duk bohong cikgu ulang balikdari awal . Bagi yang bohong pula kena penampar 2 kali.
Kesimpulannya, sesiapa yang terasa tu, insaflah dan mulakan sikap baru yang rajin buat kerja.
Sekian,terima kasih.
Posted by Avatar at 3:32 PM 5 comments
Monday, February 2, 2009
V-Info : Details About Computer Virus
Today, i will talk about computer virus more detail. If you have any opinion, we can share.
I start from definition. In computers, a virus is a program or programming code that replicates by being copied or initiating its copying to another program, computer boot sector or document. Viruses can be transmitted as attachments to an e-mail note or in a downloaded file, or be present on a diskette or CD. The immediate source of the e-mail note, downloaded file, or diskette you've received is usually unaware that it contains a virus. Some viruses wreak their effect as soon as their code is executed; other viruses lie dormant until circumstances cause their code to be executed by the computer. Some viruses are benign or playful in intent and effect ("Happy Birthday, PEKASAM!") and some can be quite harmful, erasing data or causing your hard disk to require reformatting. A virus that replicates itself by resending itself as an e-mail attachment or as part of a network message is known as a worm.
Generally, there are three main classes of viruses:
File infectors. Some file infector viruses attach themselves to program files, usually selected .COM or .EXE files. Some can infect any program for which execution is requested, including .SYS, .OVL, .PRG, and .MNU files. When the program is loaded, the virus is loaded as well. Other file infector viruses arrive as wholly-contained programs or scripts sent as an attachment to an e-mail note.
System or boot-record infectors. These viruses infect executable code found in certain system areas on a disk. They attach to the DOS bootsector on diskettes or the Master Boot Record on hard disks. A typical scenario (familiar to the author) is to receive a diskette from an innocent source that contains a boot disk virus. When your operating system is running, files on the diskette can be read without triggering the boot disk virus. However, if you leave the diskette in the drive, and then turn the computer off or reload the operating system, the computer will look first in your A drive, find the diskette with its boot disk virus, load it, and make it temporarily impossible to use your hard disk. (Allow several days for recovery.) This is why you should make sure you have a bootable floppy.
Macro viruses. These are among the most common viruses, and they tend to do the least damage. Macro viruses infect your Microsoft Word application and typically insert unwanted words or phrases.
The best protection against a virus is to know the origin of each program or file you load into your computer or open from your e-mail program. Since this is difficult, you can buy anti-virus software that can screen e-mail attachments and also check all of your files periodically and remove any viruses that are found. From time to time, you may get an e-mail message warning of a new virus. Unless the warning is from a source you recognize, chances are good that the warning is a virus hoax.
The computer virus, of course, gets its name from the biological virus. The word itself comes from a Latin word meaning slimy liquid or poison.
PLEASE COMMENT!!! dan bacalah sesungguhnya membaca adalah perkara yang paling mudah.
Posted by Avatar at 8:18 PM 0 comments
Sunday, February 1, 2009
10 Sebab Untuk Blog
Blog itu sendiri juga mempunyai beberapa jenis. Selain blog biasa yang bersifat jurnal dan peribadi, ada juga photoblog, vblog, podcast dan banyak lagi. Photoblog lebih memaparkan gambar berbanding isi, tambahan pula untuk mengambil gambar pada masa ini adalah amat mudah. Rata-rata handphone memiliki camera digital. Vblog atau disebut juga vlog pula adalah blog terkini yang memaparkan Video sebagai isi utamanya. Podcast pula adalah blog dengan keutamaan audio.
Blog juga dibina biasanya berdasarkan kepada tajuk-tajuk tertentu, seperti blog automotif, blog teknologi, blog fesyen, blog gajet-gajet terkini dan sebagainya. Walaupun begitu, blog peribadi biasanya mendahului senarai yang paling banyak dibina.
Tidak kiralah, yang mana satu anda mahu. Berikut adalah 10 sebab mengapa anda perlu mempunyai blog!
1 - EMOSI : Hidup di lokasi Urban juga metropolitan ini selalunya berada dalam keadaan sibuk, terkejar-kejar, banyak kerja, tidak cukup masa dan bermacam masalah pada setiap hari. Manakala masih belajar pula dengan masalah di tempat belajar dan kawan-kawan. Setiap orang ada masalah. Masalah harian samada yang lazim mahupun yang jarang berlaku, akan membawa kita kepada satu pembunuh senyap iaitu tekanan! (Stress!). Semakin banyak tekanan semakin parahlah emosi sehingga membawa kepada masalah psikologi!
Pada kebiasaanya, kita meredakan tekanan dengan meluahkan pada kekasih, keluarga, kawan-kawan dan rakan sekerja? Bagaimana jika semua mereka tidak ada berdekatan, atau mungkin kita sendiri tidak mahu memberitahu mereka?
Ya! Menaiplah di blog anda, luahkan perasaan marah, kecewa, benci, terkilan dan sebagainya. Dengan ini, tekanan anda mungkin sudah berkurangan. Walaupun tidak sebanyak mana mungkin, tetapi pasti ada kesannya.
Apatah lagi apabila ada maklumbalas(comment) dari kenalan online anda ataupun sesiapa yang anda tidak ketahui yang memberikan kata-kata peransang dan semangat untuk anda. Memberikan anda tip-tip mengatasi sesuatu masalah yang mungkin pernah dilalui mereka.
Selain itu, perasaan gembira juga anda boleh hebohkan di blog anda untuk di kongsikan dengan sesiapa sahaja. Bagus bukan? Blog adalah terapi emosi.
2 - EKONOMI :Ketika ini, dimana-mana juga orang akan berkata, blog boleh mendatangkan duit! Benarkah? Ramai juga yang terjebak dalam kancah ini dan kecewa, kerana blog-blog mereka gagal mendatangkan duit. Materialistik sungguh dunia hari ini.
Membuat blog yang boleh menghasilkan pendapatan bukanlah semudah yang anda fikir. Perlu ada perancangan dan ilmu dalam bidang-bidang berkaitan. Blog yang menghasilkan pendapatan adalah sama seperti berniaga, anda perlu berfikiran seperti seorang ‘businessman’. Seorang peniaga yang mempunyai perancangan dan bertindak berdasarkan keadaan.
Ada banyak cara menghasilkan pendapatan dengan blog, secara ringkasnya begini:Bina blog yang menarik dan mengemaskininya dari masa kesemasa sehingga anda mempunyai pelawat yang ramai setiap hari. Dengan pelawat yang ramai dari masa ke semasa, anda boleh menyertai program-program pengiklanan yang ada yang mana memberikan anda komisyen atau menjual iklan terus kepada sesiapa yang mahu. Selain itu, menjual blog anda kepada sesiapa yang berminat dengan harga yang tinggi. (sudah tentu bukan blog peribadi anda)
Tahukah anda, wujud satu kerjaya baru digelar “ProBlogger” iaitu ‘pemblog profesional!’
*Blog yang menjana pendapatan adalah merupakan bab yang besar dan memerlukan huraian yang jauh lebih panjang dan ruang lingkup yang luas. Saya akan buat artikel menyeluruh pada masa hadapan jika berpeluang..
3 - DIARI: Kita menulis segala yang berlaku setiap hari di dalam diari. Lazimnya perempuanlah!. Tetapi lelaki juga boleh mempunyai diari, “Diari Seorang Lelaki” mungkin.
Ingatkah kita… apa yang berlaku pada hari ini, tetapi setahun yang lalu? Sudah tentu tidak bukan? Nah.. alangkah baiknya jika semua hidup kita ada catatan. Kadangkala, saya sendiri membaca apa yang saya lakukan pada tahun lepas didalam blog saya. Ada masanya saya ketawa sendiri, juga gembira dengan perkara-perkara menarik yang dilakukan bersama kawan-kawan, ada masanya kita mungkin kagum dengan diri kita sendiri dengan apa yang kita lalui beberapa tahun lalu!.
Oh Ya!, apa yang lebih menarik, ada juga blog ibu-ibu yang merakamkan cerita dan gambar-gambar anak mereka dari saat dilahirkan, merangkak, mula bercakap perkataan pertama sehinggalah boleh berjalan mahupun sudah mula bersekolah!.
Blog mungkin ‘public diary’, bermaksud boleh di baca oleh sesiapa. Tetapi jangan bimbang, sesetengah blog mempunyai fungsi pos peribadi (private). Ada yang memerlukan kata laluan untuk dibaca!.
Setiap hari kita akan jumpa keyboard dan monitor. Kita lebih mengenal keyboard daripada pen dan buku. Jari kita lebih pantas menaip daripada menulis menggunakan pen di kertas. Atas sebab ini… tiada keraguan bahawa blog adalah diari terkini!
Seterusnya!!!!
Lagi 7 tu lain kali sajalah.
Posted by Avatar at 7:13 PM 0 comments
Tuesday, January 27, 2009
What is ALU???
Somebody want me to tell about What Is ALU ???
Short for Arithmetic Logic Unit, ALU is one of the many components within a computer processor. The ALU performs mathematical, logical and decision operations in a computer and is the last processing performed by the processor...
Once the necessary information by the ALU has been processed it is sent to the computer memory. In some computer processors the ALU is divided into two separate parts, the AU and the LU; in this case the AU performs the arithmetic operations and the LU performs the logical operations...
Give your comment about this statement.
Posted by Avatar at 3:43 PM 1 comments
What Is Computer???
Defination of computer is a device that accepts information (in the form of digitalized data) and manipulates it for some result based on a program or sequence of instructions on how the data is to be processed...
Complex computers also include the means for storing data (including the program, which is also a form of data) for some necessary duration. ..
A program may be invariable and built into the computer (and called logic circuitry as it is on microprocessors) or different programs may be provided to the computer (loaded into its storage and then started by an administrator or user). Today's computers have both kinds of programming.
Give your comment about the info.
Posted by Avatar at 8:29 AM 1 comments
Monday, January 26, 2009
Cara Membuang Virus Atau Malware
Atas permintaan seseorang yang meminta cara mengatasi malware atau virus adalah seperti berikut:-
Satu langkah yang mungkin untuk menghapuskan virus yang wujud dalam Windows XP ialah penggunaan alat yang dikenali sebagai Pemulihan Sistem (System Restore). Alat ini memulihkan registri dan fail-fail sistem yang genting kepada titik semak yang dahulu...
Seringnya, sesebuah virus akan mengakibatkan sistem komputer tergantung, dengan pembutan semula keras akan merosakkan titik pemulihan sistem daripada hari yang sama. Titik pemulihan daripada hari-hari sebelumnya harus masih berkesan, asalkan virus itu tidak direka untuk merosakkan fail-fail pemulihan. Bagaimanapun, sesetengah virus, misalnya virus CiaDoor, akan mematikan pemulihan sistem serta alat-alat lain yang penting seperti Pengurus Tugas (Task Manager) dan penggesa..
Virus mengubah suai registri dengan cara yang tepat sama dengan para pentadbir mematikan alat-alat tersebut atas berbagai-bagai alasan daripada pengguna-pengguna terhad, kecuali bahawa virus menyekat semua pengguna, termasuk juga pentadbir. Apabila sesuatu alat terjangkit diaktifkan, virus itu akan memaparkan pesanan, "Pengurus Tugas telah dimatikan oleh pentadbir anda", walaupun jika pengguna yang mencuba memulakan atur cara adalah pentadbir pada dirinya.
Selain itu, penggunaan malware removal atau antivirus amat penting bagi mengelakkan kerosakan sistem computer akibat serangan virus. Untuk mengelakkan jangkitan virus,spyware dan malware anda bolehlah membaca tentang tajuk Punca Dan Kesilapan Yang Menjemput Malware di muka hadapan blog.
Berikan pendapat atau komen selepas anda membaca maklumat di atas. Sekian,terima kasih.
Posted by Avatar at 7:12 PM 2 comments
Sunday, January 25, 2009
Punca Dan Kesilapan Yang Menjemput Malware
Malware berasal daripada perkataan malice dan software merujuk kepada perisian yang direka bagi membolos atau merosakkan sistem komputer tanpa kebenaran secara jelas daripada pemilik...
Jangkitan malware boleh berlaku jika anda mengunjungi tapak web yang menawarkan bahan - bahan negatif. Atau , jika anda menggunakan aplikasi yang dikaitkan dengan bahan negatif...
Berikut adalah punca dan kesilapan yang mengundang malware:-
- Bahan berunsur porno
- Movie dan muzik haram (MP3)
- Perisian cetak rompak
- Perisian ' peer - to - peer' (P2P0
- Asakkan iklan internet
- Perisian sekuriti palsu
- Perisian percuma berisiko
- Tapak web dan skrip merbahaya
- Kesilapan pengguna emel
- Kelalaian pengguna PC
Setelah mengetahuinya, anda perlu mengambil langkah proaktif yang relevan...
Sila berikan komen jika terdapat sebarang kesilapan dan kesalahan fakta diatas.
Posted by Avatar at 9:29 AM 2 comments
Labels: Malware
Saturday, January 24, 2009
History Of Computer
Yesterday, i had told to you about information computer but today i want to tell about History Of Computer.It is difficult to identify any one device as the earliest computer, partly because the term "computer" has been subject to varying interpretations over time...
Originally, the term "computer" referred to a person who performed numerical calculations (a human computer), often with the aid of a mechanical calculating device.
The history of the modern computer begins with two separate technologies - that of automated calculation and that of programmability.
Examples of early mechanical calculating devices included the abacus, the slide rule and arguably the astrolabe and the Antikythera mechanism (which dates from about 150-100 BC).
Hero of Alexandria (c. 10–70 AD) built a mechanical theater which performed a play lasting 10 minutes and was operated by a complex system of ropes and drums that might be considered to be a means of deciding which parts of the mechanism performed which actions and when.This is the essence of programmability....
The "castle clock", an astronomical clock invented by Al-Jazari in 1206, is considered to be the earliest programmable analog computer. It displayed the zodiac, the solar and lunar orbits, a crescent moon-shaped pointer travelling across a gateway causing automatic doors to open every hour,and five robotic musicians who play music when struck by levers operated by a camshaft attached to a water wheel...
The length of day and night could be re-programmed every day in order to account for the changing lengths of day and night throughout the year.
The end of the Middle Ages saw a re-invigoration of European mathematics and engineering, and Wilhelm Schickard's 1623 device was the first of a number of mechanical calculators constructed by European engineers.
However, none of those devices fit the modern definition of a computer because they could not be programmed...
Posted by Avatar at 7:38 AM 1 comments
Labels: History
Friday, January 23, 2009
Informotion About Computers
If you want to know detail about computer, i will tell about it...
A computer is a machine that manipulates data according to a list of instructions...
The first devices that resemble modern computers date to the mid-20th century (1940–1945), although the computer concept and various machines similar to computers existed earlier..
Early electronic computers were the size of a large room, consuming as much power as several hundred modern personal computers PC.Modern computers are based on tiny integrated circuits and are millions to billions of times more capable while occupying a fraction of the space.
Today, simple computers may be made small enough to fit into a wristwatch and be powered from a watch battery. Personal computers, in various forms, are icons of the Information Age and are what most people think of as "a computer"; however, the most common form of computer in use today is the embedded computer....
Embedded computers are small, simple devices that are used to control other devices — for example, they may be found in machines ranging from fighter aircraft to industrial robots, digital cameras, and children's toys....
The ability to store and execute lists of instructions called programs makes computers extremely versatile and distinguishes them from calculators. The Church–Turing thesis is a mathematical statement of this versatility: any computer with a certain minimum capability is, in principle, capable of performing the same tasks that any other computer can perform. ..
Therefore, computers with capability and complexity ranging from that of a personal digital assistant to a supercomputer are all able to perform the same computational tasks given enough time and storage capacity and that all for today. Thank you.
Posted by Avatar at 7:38 AM 1 comments
Thursday, January 22, 2009
Disadvatanges Of Using Mobile Phone
Since the introduction of mobile phones, concerns (both scientific and public) have been raised about the potential health impacts from regular use...
But by 2008, American mobile phones transmitted and received more text messages than phone calls...
Numerous studies have reported no significant relationship between mobile phone use and health, but the effect of mobile phone usage on health continues to be an area of public concern...
For example, at the request of some of their customers, created usage controls that meter service and can switch phones off, so that children could get some sleep...
There have also been attempts to limit use by persons operating moving trains or automobiles, coaches when writing to potential players on their teams, and movie theater audiences....
By one measure, nearly 40% of automobile drivers aged 16 to 30 years old text while driving, and by another, 40% of teenagers said they could text blindfolded..
Posted by Avatar at 9:20 PM 0 comments
My New Blog
Now i has one weblog.
My teacher suggest to start blogging..
thanks to him for teaching me to start blog..
And now i am blogger..
That all for today.
Posted by Avatar at 4:32 PM 2 comments
Labels: read

